Function aes_frast::aes_with_operation_mode::cfb_enc
[−]
[src]
pub fn cfb_enc(
plain: &[u8],
cipher: &mut [u8],
keys: &[u32],
iv: &[u8]
) -> Vec<u8>
CFB (Cipher Feedback) Encryption
The feedback size is fixed to 128 bits, which is the same as block size.
This mode doesn't require padding.
This function encrypts a long plain from the first parameter and put the long cipher
into the second parameter, using the scheduled keys and the initialization vector (IV)
in the third and fourth parameters.
Finally, it returns the final block of the cipher (NOT the plain).
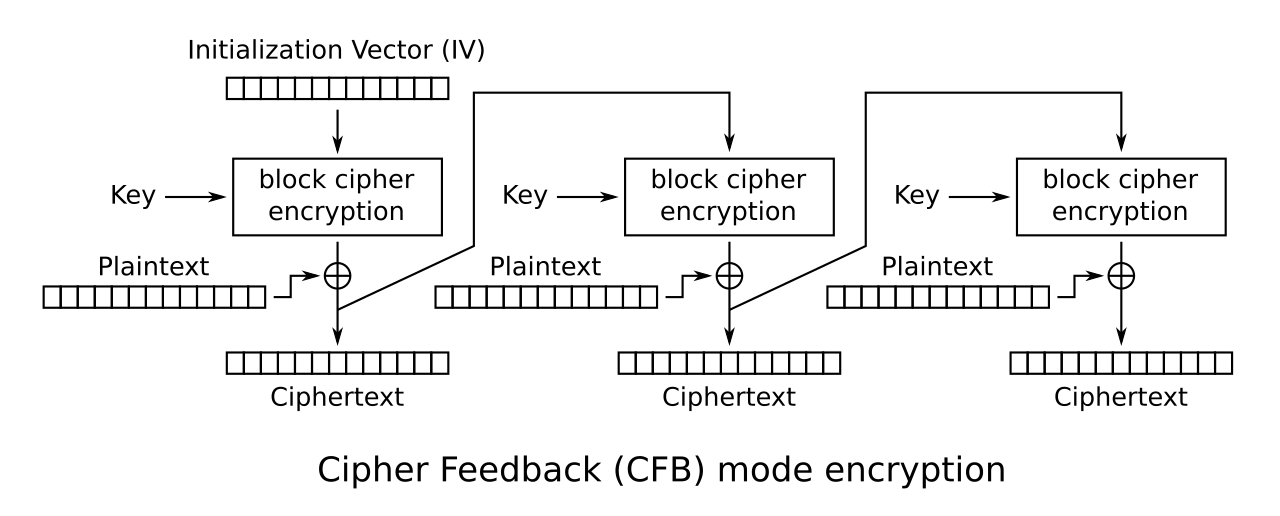 (This picture comes from the Wikimedia Commons)
(This picture comes from the Wikimedia Commons)
Examples
use aes_frast::{aes_core, aes_with_operation_mode, padding_128bit}; let length: usize = 64; let mut plain: Vec<u8> = vec![0x34, 0x63, 0xD0, 0x89, 0x1D, 0x71, 0x4A, 0xB0, 0x08, 0x5D, 0x22, 0xE1, 0x8B, 0xFA, 0x77, 0xF0, 0xEB, 0xE4, 0xB8, 0x9E, 0xF0, 0x05, 0x32, 0x7D, 0x4F, 0xBD, 0x87, 0x69, 0x75, 0x76, 0x78, 0xAA, 0x3D, 0x24, 0x06, 0x0C, 0xA4, 0xA5, 0x8C, 0xA0, 0x21, 0x58, 0xB8, 0xA1, 0x86, 0xAD, 0xBB, 0x6D, 0x9E, 0x09, 0x1C, 0x47, 0x06, 0x25, 0x4B, 0x2E, 0x30, 0x53, 0x3A, 0x5F, 0xE9, 0xDF, 0x3A, 0x90]; let mut cipher = vec![0u8; length]; let mut dec_cipher = vec![0u8; length]; let mut o_key: Vec<u8> = vec![0x0F, 0x57, 0x9F, 0x79, 0x50, 0x99, 0x0A, 0xCE, 0x66, 0x72, 0xA8, 0x17, 0x95, 0x1F, 0xF6, 0x06, 0x24, 0x40, 0xDE, 0xF5, 0x08, 0xF1, 0x64, 0x34, 0xD6, 0xEF, 0xEF, 0xFD, 0x26, 0x23, 0x04, 0x95]; let mut w_keys: Vec<u32> = vec![0u32; 60]; let mut iv: Vec<u8> = vec![0x04, 0x7C, 0xF3, 0xEA, 0xE1, 0x76, 0x45, 0x85, 0x72, 0x52, 0x7B, 0xAA, 0x26, 0x0D, 0x65, 0xBB]; aes_core::setkey_enc_auto(&o_key, &mut w_keys); aes_with_operation_mode::cfb_enc(&plain, &mut cipher, &w_keys, &iv); let expected_encrypted = vec![0x9D, 0xF9, 0x3D, 0x71, 0xC1, 0x9E, 0x50, 0x22, 0x36, 0x35, 0xF1, 0xB6, 0xED, 0xA6, 0x86, 0x74, 0x5F, 0x34, 0xD6, 0x93, 0xA9, 0x0F, 0xFF, 0x50, 0x4C, 0xE6, 0x8E, 0xC0, 0x06, 0x3F, 0x3A, 0x62, 0x78, 0x9F, 0xAB, 0xB1, 0x06, 0x95, 0x64, 0xB6, 0xBB, 0x06, 0x92, 0x02, 0x34, 0x2D, 0x36, 0x35, 0xA4, 0x95, 0x30, 0x2E, 0x20, 0xD3, 0xE8, 0x53, 0x95, 0xA2, 0xDF, 0x83, 0x9B, 0x7B, 0x12, 0x3F]; assert_eq!(length, cipher.len(), "ERROR cipher.len()"); for i in 0..length { assert_eq!(expected_encrypted[i], cipher[i], "ERROR in encrypt {}", i); } // Notice: CFB only uses block-encryption, no matter we use it as encryption or decryption. // So, keep don't use functions which start with`setkey_dec_` and keep the next line commented out. //aes_core::setkey_dec_auto(&o_key, &mut w_keys); aes_with_operation_mode::cfb_dec(&cipher, &mut dec_cipher, &w_keys, &iv); assert_eq!(length, dec_cipher.len(), "ERROR dec_cipher.len()"); for i in 0..length { assert_eq!(plain[i], dec_cipher[i], "ERROR in decrypt {}", i); }